Day three turned out to be great. I had planned four sessions, two in the morning and two in the afternoon, with only one focusing on the topic of AI. The sessions proved to be interesting, and the content is easily applicable to life back home.
Today, I attended the following sessions:
- State of the CISO 2024: Doing More with Less
- Data-Driven Cyber Indicators of Malicious Insider Threat
- You’re doing it Wrong! Common Security Anti Patterns
- Beyong the Hype: Research on How Cybercriminals are Really Using GenAI
State of the CISO 2024: Doing More with Less
Based on the talk’s description and title, I expected the presenters to discuss strategies and tactics for working with a small budget. However, the session focused on Nicholas Kakolowski and Steve Martano presenting the State of the CISO 2024 report published by their company. The report examines data and trends related to the role of the CISO in the US without drawing real conclusions. Data comes from their own American consulting business and when asked about plans to include other continents, the presenters stated that Europe is less advanced than the US, indicating a narrow American perspective. I found Steve’s delivery of this message quite arrogant and my expectation is that they just don’t do business outside of the US. Nonetheless the presented statistics might be interesting (to be honest I have my doubts on some of the methodologies used to obtain the statistics).
In the US, only 20% of CISOs are at the C-level. Most CISOs are at the executive, director, or VP level. More responsibilities are getting added to the role though. While topics like privacy and fraud are often shared responsibilities with other departments. In the case of GenAI, most CISOs have the full responsibility to make the risk decisions for the business.
Not all CISOs are even reporting to the board. The report concludes that when CISOs aren’t often reporting or not-at-all reporting to the board, they are less satisfied with the board’s budget decisions and their mandate (neutral responders were removed from the dataset, however, so the question is how statistically significant this is).
Budget trends
The growth in the budget for Cyber Security has declined, as has the money available for staff. However, we must consider this in the context of the overall market, where budgets have been declining. The fact that the budgets on average still grow is a good sign. It indicates that businesses consider Cyber Security important, but there are limitations on how much they can spend on it.
The budgets have made it harder to hire. Around 38% of the budget can be spent on hiring, and given the salaries for security personnel in the US, it is difficult to fill vacancies. Often, more than 1000 people apply, but only 10 are qualified, and they are too expensive for the budget.
Retaining your team
A large number of people don’t feel valued and supported, or are unsatisfied with career opportunities. The issue arises after 4-7 years. In the first 2 years, the job is still interesting and exciting. By the third year, people start to get bored, and by year 4, they leave. As hiring is difficult, it is important to ensure that your team feels valued and to create career paths within the organization.
Data-driven Cyber Indicators of Malicious Insider Threat
The MITRE Institute conducted applied behavior science research to better understand the behavior and potential risk indicators for insider threats. In a track session, James Doodson explained the methodology used and shared the conclusions from this research. Unfortunately, time was limited, and James had to rush through the slides, which meant he wasn’t able to discuss most of the details of the research. As this is a very interesting research, I would recommend taking a look at the slides for more details.
Research questions
- How can malicious insiders exfiltrate sensitive information and evade detection?
- Are the Potential Risk Indicators (PRIs) different between remote and on-premises environments?
- Are there specific sequences of behavior which are useful PRIs for insider risk?
Methodology
MITRE assigned 150 individuals to perform a series of sensitive tasks on the live corporate network. These individuals had to carry out these tasks over a span of a week while also performing their regular duties. The tasks involved searching for sensitive information, collecting it, and exfiltrating it. The organization divided the 150 people into three groups:
- Benign users: these users had the task of sending the sensitive information to their client
- Malicious users: these users had the task of sending the sensitive information to a competitor to improve their job prospects
- Super malicious users: these users had the same task as the malicious users, but these individuals were highly cyber-savvy employees with a technical background
MITRE collected data using network and host-based sensors over a period of three weeks: one week before exfiltration, the week of exfiltration, and the week after exfiltration. The participants kept a logbook of when they performed their tasks, so that the researchers could disregard data about the participants’ regular work.
Additionally, the researchers used questionnaires and interviews to capture activities that were not visible in the network and endpoint sensor data.
1. Identifying exfiltration and evasion techniques
The researchers identified 13 exfiltration techniques and 11 sub-techniques that the participants used. Users with the benign user role used 6 of these techniques as well, such as sending attachments over email or uploading files to cloud storage. These indicators are useless for identifying a malicious insider.
Malicious insiders used 9 unique techniques and sub-techniques, including printing hard copies (often done with personal printers at home), using removable media, and creating burner email accounts. These techniques might be useful potential risk indicators (PRIs).
Super malicious insiders also used 9 techniques and sub-techniques unique to their group, such as adding the data to source code they would normally write and then uploading that to Github. Most of these techniques make use of techniques these people also use during their normal work, making it difficult to use them as individual PRIs.
Participants used 76 different exfiltration techniques. Interestingly, regular malicious users use similar techniques as the tech-savvy ones. The tech-savvy insiders know the controls in place and use simple techniques when they think that is good enough. Also, don’t underestimate untrained people; they can find out a lot through Google.
MITRE draws three conclusions based on these results:
- There is no difference in the amount of time spent for the task between a benign vs malicious user.
- Odd working hours are NOT a good PRI.
- Focus on early behavior in the searching and gathering phases rather than on the exfiltration.
2. Remote vs On-premise
Remote and on-premise users show no difference. The same potential risk indicators (PRIs) can be used to detect insiders in both cases.
3. Sequence of steps
In previous research, MITRE focused on analyzing steps used together. This time, MITRE attempted to determine if the order of these techniques makes a difference. In total, the researchers found 5 million permutations between PRIs. The final set only contains 5 sequences for malicious users and 7 sequences for super malicious users.
Interesting sequences that the researchers found:
- Malicious insiders tend to persistently attempt to access a file in Sharepoint after receiving an access denied message, while benign users do not exhibit this behavior.
- Malicious insiders frequently move from one file to another, exfiltrating each file before moving on.
From this research, MITRE identified that External Threat Frameworks are ineffective for addressing insider threats. In response, MITRE is working on developing new strategies specifically tailored to combat insider threats.
You’re doing it wrong! Common Security Anti Patterns
This was a surprisingly interesting talk. Initially, I didn’t have high hopes for this session as both speakers are from Microsoft. However, they did a good job and effectively introduced the topic of Security Anti Patterns without promoting Microsoft. They shared some interesting patterns that I could definitely recognize happening in real life. I won’t be discussing all patterns in this summary, and I highly recommend taking a look at the slides yourself and watching the recording if you have the opportunity.
First, what is an anti pattern? An anti-pattern is a common response to a common problem that is either counterproductive or ineffective. The idea of collecting anti-patterns is to create a common language to recognize these patterns and define best practices for avoiding them.
Groundhog day incidents
Groundhog day incidents are recurring incidents that require the SOC to conduct the same investigation repeatedly. The root causes for these incidents are two anti-patterns:
- Technology-Centric Thinking: This involves viewing Cyber Security as solely a technology problem and relying on technology, rather than focusing on processes and people.
- Silver Bullet Mindset: This refers to the belief that a single solution will completely solve a complex or ongoing problem. Silver Bullet thinking is more common than one might expect. For instance, assuming that patch management is the solution simply because the incident started with CVE-xxx is an example of the silver bullet mindset. It’s important to be mindful of these hidden moments of silver bullet thinking!
The paradox of blame
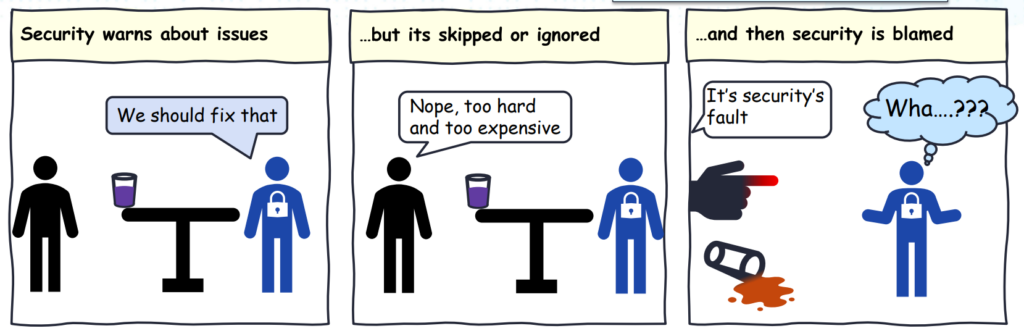
Blame leads to fear, which in turn leads to a “cover your ass” mentality. The solution is to adopt a blameless approach. It’s important to be kind to your colleagues and communicate in a direct and honest manner.
Downwards spiral
There is a downwards spiral between two anti-patterns:
- Department of No: The CISO department doesn’t align with the business and focuses solely on achieving 100% security, resulting in frequent rejections of business initiatives.
- Delay Security Until the End: Due to the constant rejections from the security department, the business either delays or bypasses security considerations.
These two anti-patterns reinforce each other. By delaying security until the end, the CISO department loses the ability to influence the approach and ends up frequently rejecting proposals. This, in turn, hinders the business, leading them to avoid involving security early on.
The way to break this cycle is similar to addressing the Paradox of Blame: be kind and try to understand each other. From the cybersecurity side, ask questions such as “How can I help you achieve your objectives securely?” and encourage open communication.
Bizarre risk exceptions
Granting permanent risk exceptions for business-critical workloads for political reasons, such as fulfilling a request from the CEO, can be detrimental. Just as fire can burn down a factory regardless of where it starts, the same is true for cybersecurity. It’s important to prioritize security measures to protect against potential risks, regardless of political pressures.
Continuous simplicity and create clarity
If we cannot create simplicity and clarity, we have already lost the battle. Clarity begins at the policy level. Policies should be written for people; if people don’t understand the policy, how can we implement it? It always starts with a clear and simple policy, and the complexity arises from implementing that policy into technology.
Overcoming anti patterns
Focus on security outcomes. The goal is to thwart attackers and increase resistance. Increasing resistance can be achieved by thwarting simple attacks and ensuring swift responses. Change your language: you are not just protecting a network, you are safeguarding business assets.
Invest wisely. When an attacker gains privileged access, the situation can deteriorate rapidly. The same applies when critical assets are compromised. This is where your protections should begin. Prioritize Identity, Endpoint, and Email security before focusing on Network security.
Enhance collaboration between teams. This can be achieved by establishing mutually beneficial arrangements. Provide engineering and Ops teams with technical summaries of attacks to help them prevent future attacks. This will help the SecOps team avoid recurring incidents. For the business, provide summaries of attacks to provide leadership with insights into real-world attacks, while also increasing the SecOps team’s awareness to fulfill their mission.
Beyond the Hype: Research on how cyber criminals are really using GenAI
This was the last track session of the day and I found it quite a refreshing one. Yes the topic is AI, but this session also brings everything back in perspective. What are cyber criminals actually using and what is just speculation?
To be fair, malicious AI already existed for a long time. Mostly being used in poker bots and other bots. In this talk the focus was mostly on Generative AI and the use by criminals.
Malicious code generation
This doesn’t work that well yet. Large Language Models (LLMs) are capable of generating basic code samples and exploits. However, cyber criminals already possess these capabilities, so there is no need for that. LLMs are not yet proficient at creating more complex code, and therefore there appears to be limited utility in using GenAI to generate malicious code.
Malicious tools with AI capabilities
One thing that we do see is the addition of AI capabilities to existing criminal tools. These additional capabilities generally focus on generating phishing messages and using them in conversations with victims.
Criminal LLMs: Worm GPT
Only one true attempt at a criminal LLM was created. This information is known because the author publicly wrote about it on underground forums. However, after being put up for sale in June 2023, the creator discontinued it in August 2023.
Scams
More seemingly criminal LLMs are being sold on underground forums. Upon further inspection, most of these appear to be scams. They quickly disappear after a week or make outrageous claims about their capabilities. It is still one of the favorite activities of criminals: scamming, even among thieves.
Jailbreak as a service
Jailbreaks are methods used to deceive a LLM into bypassing its protections, enabling a user to exploit it for malicious purposes. LLM creators are prompt to patch jailbreaks when they become aware of them, leading to the continuous development of new jailbreaks. Keeping track of these jailbreaks can be tedious for a criminal, hence the emergence of jailbreak-as-a-service. This service monitors jailbreaks and enables attackers to seamlessly utilize the latest jailbreaks.
Jailbreaks also render criminal LLMs unnecessary. When needed, regular LLMs can be used for malicious purposes. Moreover, most lucrative cyber attacks involve social engineering, which can be fully executed using commercially available legitimate LLMs.
Deep Fakes
The market has recently seen an increase in offers. Criminals are now offering ways to use deep fake technology to bypass KYC processes that require a selfie with a photo from your password. GenAI is proficient at replacing your face with that of somebody else, making such attacks easy.
GenAI is used for extortion in relation to deep fakes. For instance, criminals use AI to create a clone of a child’s voice and use it to fake a kidnapping scenario. Another common use, which was mentioned during the main stage keynote, is sextortion, where fake nude pictures are created of mostly young boys to extort them.
Leave a Reply