It is the second day of RSA and we continue to hear everyone rehash the same Generative AI statements. There is basically three type of comments that almost every session, and keynote speaker follows:
- I have a talk about something completely different, but AI is popular so here is my mandatory AI statement
- I had ChatGPT generate this bad joke and I must share this with the audience (even the central keynote speakers make this mistake)
- My talk has generative AI as a topic, but I am not an expert so I stay with generic, handwavy statements
Despite of the AI annoyance it was a great day. I joined three track sessions and all three of them were great.
- Gartner’s top predictions for Cyber Security 2023 / 2024
- Lessons Learned: General Motors Road to Modern Consumer Identity
- Unveiling the 2024 Data Breach Investigation Report (DBIR)
Gartner’s top predictions for Cyber Security 2023 / 2024
Leigh McMullen from Gartner presented seven predictions for the coming years. Before he presented these he showed a few previous predictions as well. Conclusion from these examples is that predictions are a bit hit or miss. So even though these predictions are based on data and Gartner analyst experience, you have to take them with a grain of salt.
Prediction 1: By 2024 modern privacy regulation will cover the majority of consumer data
Of course, we’ve had GDPR in Europe for quite some time now. Gartner predicts that the rest of the world, including the US, will catch up this year. This implies that privacy will become even more important, and consumers will start looking at companies for their respect for privacy.
An interesting statement from Gartner is that only 10% of organizations “weaponize” privacy to gain a competitive advantage. They gave examples of this “weaponization” with Google and Apple. Google, for instance, had the “don’t do evil” statement in their strategy for a long time, which led to a lot of trust in the company. Despite this, they still sell customer data, but people still love Google. Another example is Apple, which has a strong focus on privacy and uses it in much of their marketing. Their market share has been increasing based on this privacy directive.
Prediction 2: By 2025 nearly half of the people in the cyber security space will change jobs. 25% of these change to different roles entirely
The Cyber Security world has been experiencing high levels of stress and pressure. The shift to hybrid working has further intensified this pressure, as the boundary between work and private life becomes more vague, making it difficult to disengage. To prevent this prediction from becoming a reality, we need to change the rules of engagement and prioritize the mental health of our people.
Gartner recommends focusing on a culture shift that leans towards empowering autonomous, risk-aware decision-making, allowing the security team to concentrate on what truly matters.
Tracking Human Error is a valuable KPI. An increase in human errors indicates that the team is overloaded, prompting the need to consider hiring more people or reducing the workload of the security team.
Prediction 3: By 2025 50% of cyber security leaders has tried unsuccessfully risk quantification to drive decision maker
Leigh was very clear about this prediction: Risk Quantification is a fool’s errand. Measuring probability and outcome is impossible. His recommendation is to focus on Outside-in threat quantification, using business assets instead of scenarios as the basis for quantification. This approach aligns with how businesses have traditionally operated, leveraging existing business cases.
You can assess Denial of Service, Tampering, Exfiltration, and Theft, and map these against your value chain and assets. It’s much easier for the business to articulate the impact of downtime on a critical value chain, as these values have already been calculated in the past.
Prediction 4: By 2025 50% of cyber leaders will attempt zero trust, but only 25% will realize its value
Implementing Zero Trust is challenging, and realizing its value is even more so. Gartner recommends focusing your Zero Trust implementation on three zones—your systems of innovation, systems of record, and systems of differentiation—instead of attempting to cover everything.
Typically, systems within the same zone work closely with each other. By establishing these zones, you can ensure greater flexibility for innovation without impacting your business systems.
Following the zoning, Zero Trust becomes a continuous effort. It’s important to recognize that Zero Trust is not a one-time investment or a product that can be purchased; rather, it is a vision for Cyber Defense.
Prediction 5: By 2025 60% of cyber defense tools will leverage Exposure Management data to validate, prioritize and detect threats
Traditional detection solutions will struggle to keep pace with this trend, and the transition to modern solutions like XDR (eXtended Detection and Response) will accelerate. Leigh recommends exploring the Cyber Security Mesh Architecture.
Prediction 6: By 2026 70% of boards will include one member with cyber security knowledge
It’s important to remember that there are “imposters”—individuals currently serving on company boards who believe they understand Cyber Security, but in reality do not. Gartner recommends identifying these individuals and providing them with training to deepen their understanding of Cyber Security.
Currently, there are very few CISOs in the world (Leigh mentioned he doesn’t know a single CISO) who are Board Qualified and capable of making independent decisions about the company without facing termination. Typically, only the CEO and CFO hold this level of authority. Therefore, it is advisable to clearly define who is truly responsible and therefore legally liable in the event of a breach.
Prediction 7: By 2027 75% of employees will create, acquire or modify technology outside of ITs visibility
This is a trend that is already underway. While it may be unstoppable, there are ways to embrace it. For instance, rather than providing a fully capable computer with maximum access, we could restrict access. Leigh humorously mentioned that the Xbox is the most secure Windows computer because it has restricted access. Most end users don’t require the ability to directly interact with a socket or encrypt a disk. By limiting this access and offering users Low Code solutions to build their own apps, we can still manage the threat landscape while adapting to this trend.
Prediction 8: By 2027 50% of CISO’s have a Human Centric security practice
A control that is bypassed is worse than having no control at all. Therefore, a human approach to cybersecurity is essential. Security teams will need to be more actively involved in solution design and development, enabling them to create controls that align with the business and user needs, ultimately reducing friction.
Leigh has a typical American, over-the-top presentation style, which can be a bit overwhelming for us Europeans. However, the content of this talk was very interesting, and I would definitely recommend watching the recording if you can.
Lessons Learned: General Motors Road to Modern Consumer Identity
Andrew Cameron, an Enterprise Architect at General Motors, and Razi Rais, a Product Manager at Microsoft, led this session. They divided the session into two parts, with Andrew sharing General Motors’ experiences in implementing a modern identity for consumers, followed by Razi delivering a sales pitch for Microsoft.
Andrew, from General Motors, shared some interesting insights. Firstly, he highlighted that consumer identities differ from corporate identities in four key ways:
- Creation: The process for creating a consumer identity differs from that of a corporate user. For consumer identities, it’s important to reduce friction to keep the user engaged, while for corporate identities, roles within the organization need to be defined.
- Proofing: The methods for verifying a consumer identity differ from those for a corporate user.
- Business focus: The business focus of a consumer account is different from that of a corporate user.
- Branding needs: Consumer-facing identities have greater branding needs compared to corporate accounts.
Security is a delicate balance for consumer identities. It’s important to ensure security while minimizing friction. This is crucial for mandatory MFA and the types of logins allowed.
General Motors shifted from a product-first to a customer-first approach. Instead of focusing on people who own a car, they now view individuals as customers who can potentially use multiple products.
This shift also impacted their approach to identity. They now establish a centralized identity for a user but separate the user profile for specific apps the user is using.
Microsoft initiated the conversation by outlining how an identity pipeline should be structured:
- Establish Intent: what does the identity want and why?
- Establish Proof: is the user who they say they are?
- Observe
- Orchestrate.
For General Motors, this concept looked like the diagram below:
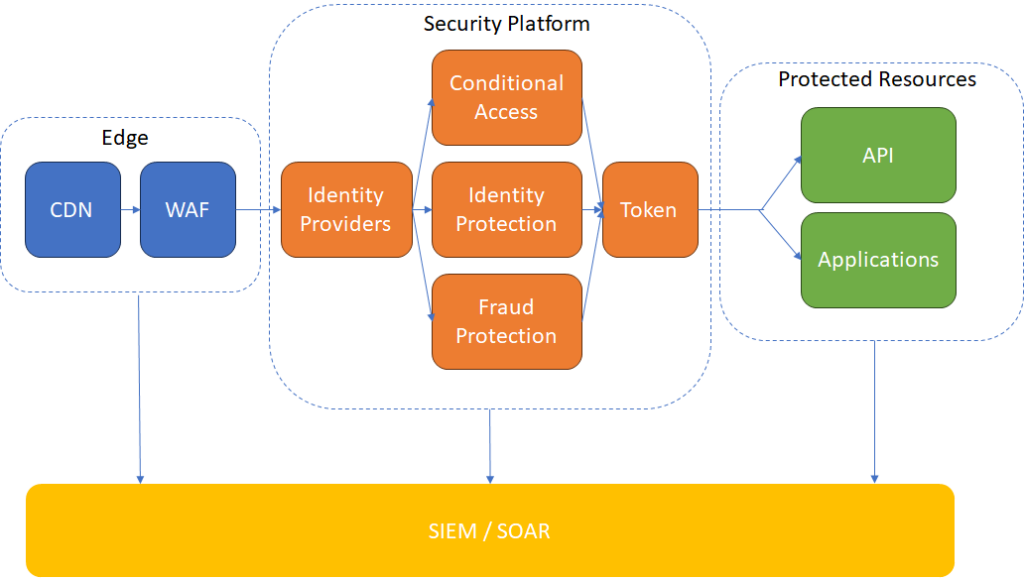
The intent is determined at the edge, where the WAF helps filter out bots and clearly malicious requests. The Security Platform is responsible for establishing proof of whether the user is who they claim to be. The concept of Observe and Orchestrate involves using SIEM + SOAR to track user behavior throughout the process and respond later, such as by enforcing MFA or removing a user account entirely.
I appreciate the diagram and the architecture used by General Motors. However, the original slides heavily focused on Microsoft. While the start of the session was very interesting, it eventually turned into a demo session of Microsoft tools that can achieve this architecture. It should be feasible to achieve a similar architecture with other tools, and in the final diagram, I changed the names to more generic terms.
Despite the Microsoft sales pitch, I would recommend watching at least the first 30 minutes of this session if you have the chance.
Unveiling the 2024 Data Breach Report
Chris Novak presented the key findings of the Verizon Data Breach report for 2024, which was released last week. Even outside of the RSA session, this report comes highly recommended.
The Verizon Data Breach report provides an analysis of over 30,000 cybersecurity incidents and 10,000 data breaches. Verizon gathers its data from its own incident response team and over 100 partners, providing a solid foundation for drawing conclusions.
In the past year, the exploitation of vulnerabilities increased by 180%, and breaches involving a non-malicious human element increased by 68%.
The median loss for breaches involving ransomware or extortion was $46,000, while the median loss for Business Email Compromise (BEC) was $50,000. Although these figures may seem low, the dataset includes many small and medium businesses that cannot afford large sums of money, leading cybercriminals to adjust their demands. This also implies that the cost of a breach for large corporations will be significantly higher.
The top three vulnerabilities identified were:
- Credentials: Primarily affecting web applications. Despite organizations implementing MFA, they often overlook “non-critical” assets, leading to their involvement in data breaches due to flat networks and lack of segmentation.
- Phishing: Surprisingly, the majority of phishing attacks still occur through email.
- Exploits: As previously mentioned, these incidents increased by 180% over the past year.
Speed in addressing these vulnerabilities is crucial. Attackers are becoming faster at scaling and exploiting newly discovered vulnerabilities, while organizations are still slow in resolving them. On average, it takes 55 days to address 50% of all new vulnerabilities. To prioritize, Verizon recommends using risk quantification to determine which vulnerabilities to address first. For example, Internet-facing medium-risk vulnerabilities might be more important to resolve than critical vulnerabilities on systems deep within the network that are difficult to access.
Verizon also presents a graph showing reported phishing attacks. The total percentage of people who did not click and reported, combined with those who clicked and reported, is around 20% of all phishing emails. While this figure should be higher, the positive aspect is that the trend is moving in the right direction.
This year, Verizon introduced a differentiation between Ransomware and Extortion. Ransomware is defined as the traditional form where data is encrypted, while extortion involves the direct extortion of individuals or the threat to leak confidential information of the organization. Interestingly, the trend shows a decrease in traditional ransomware (indicating that controls are effective), but a sharp increase in extortion.
Lastly, I’d like to share the joke at the end of the report. Although Verizon did not observe significant involvement of Generative AI in the breaches, they felt compelled to include something due to the current hype, leading to the following picture.
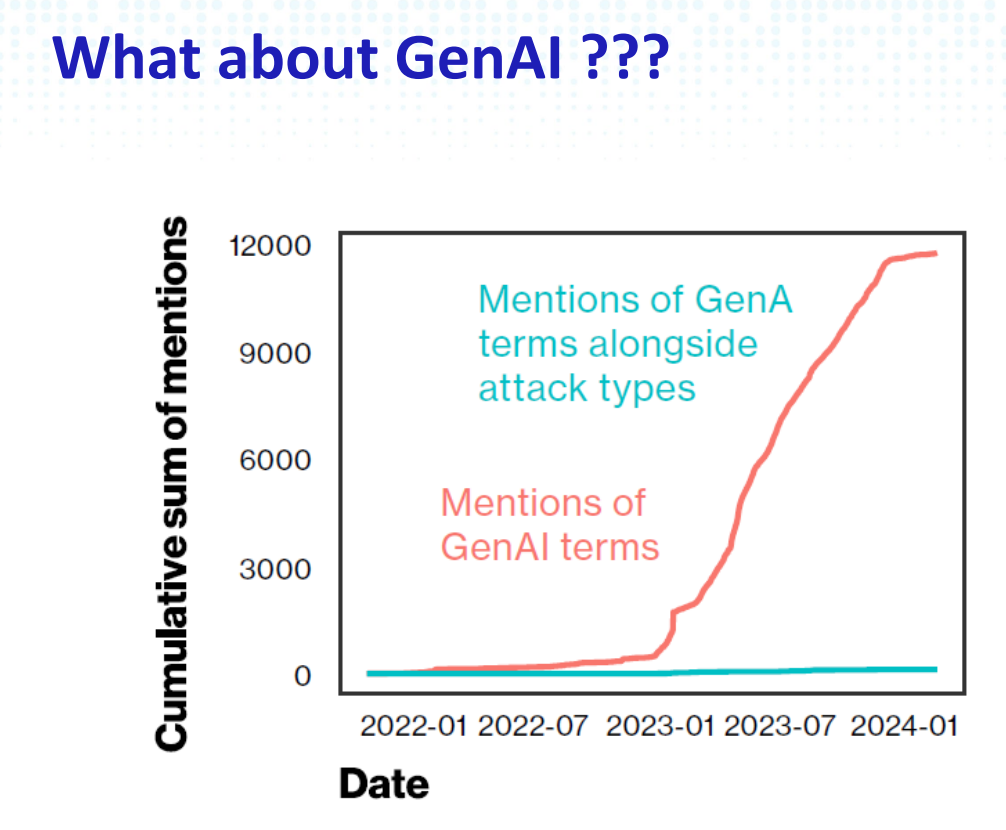
Overall, this was another excellent session. While it served as a summary of the Verizon Breach Report, I would recommend reading the actual report. However, if you’re short on time or prefer not to read through a lengthy document of 100 pages, the session provided a well-presented summary.
Leave a Reply